dnSpy 6.1.4 Download
You are about to download dnSpy, Latest Version (6.1.4) for your PC. Click the button below to start downlaoding it:
All you need to know about this download
- After clicking on "Start the Download" your file will be download from publisher's server
- This software is scanned using 58 antivirus apps. ( Check VirusTotal Scan Report )
- This file is untoched and is same as of the official site. NearFile don't touch any files no mattter what!
About dnSpy
Table of Contents
Introduction
dnSpy is a versatile open-source .NET decompiler, debugger, and assembly editor. If you want to dive deep into the .Net assemblies, dnSpy can be your best solution whether you want a free tool for debugging, reverse engineering, or enhancing existing applications. Want to learn about this wonder portable debugger? Then you are at the right place. In this article, we will talk about all the nits bits of dnSpy and how it can “byte” into your coding adventures!
Table of Contents
What Is dnSpy?
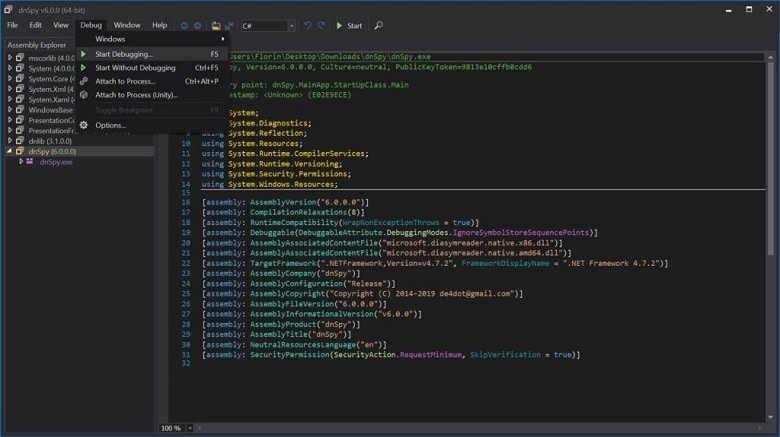
If you are looking for a Swiss Army knife for all things .Net, then dnSpy can be your sidekick. Brain child of Pavel Bouvrie since 2010, It is a debugger and assembly editor that can do the work even if the source code is not available. It relies on Idlib for reading and writing assemblies, ensuring it can deal with tricky, scrambled assemblies (like malware) without crashing.
The tool is the beating heart of the .NET community with over 1 million downloads and a thriving GitHub repository. It is like a magic decoder ring, peeling back the layers of .NET assemblies and revealing their secrets in beautifully readable C# or VB.NET code. Of course, there is more to it than just decompiler. It is your debugging buddy too. Attach it to running processes, set breakpoints, and navigate code like a seasoned detective. It’s like having X-ray vision for debugging.
What Does dnSpy Do?
dnSpy is a robust tool for working with .NET assemblies. It does a myriad of things including:
Decompilation:
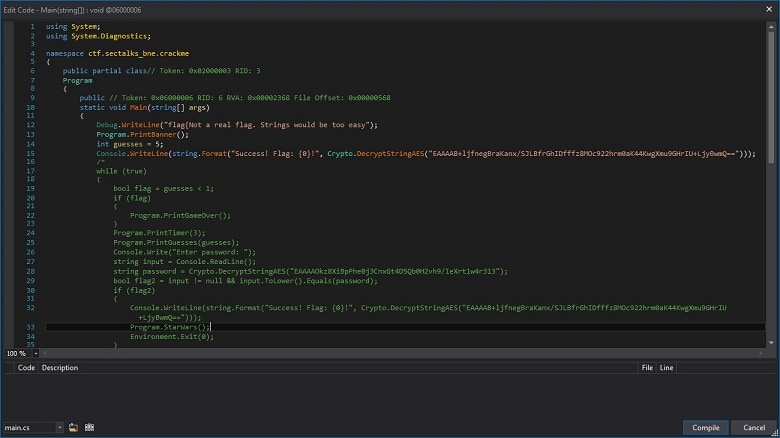
It can reverse-engineer .NET assemblies, transforming them into readable C# or VB.NET code. This feature is instrumental in understanding the inner workings of applications, even without access to the original source code. The decompiler also supports a variety of deobfuscation techniques, making it easier to reverse engineer complex malware samples.
Debugging:
The tool offers comprehensive debugging capabilities, allowing users to attach to running processes, set breakpoints, inspect variables, and step through code. Both managed and mixed-mode debugging are supported, making it suitable for complex debugging scenarios.
Assembly Editing:
It allows users to not only view but also modify assemblies. This feature is handy for making minor changes or addressing security vulnerabilities in third-party assemblies. However, caution is advised when editing assemblies to prevent unintended consequences. The assembly editor also supports a variety of advanced features, such as IL editing and metadata editing.
Assembly Analysis:
It provides detailed insights into assemblies, including their classes, methods, and fields. This analysis is invaluable for comprehending the structure and dependencies of an application.
Expression Evaluator:
The dnSpy expression evaluator allows users to evaluate C# expressions at runtime. This feature can be used to test code snippets, debug expressions, and inspect the state of running applications.
Extension Support:
The free tool can be extended with plugins to enhance functionality. A vibrant community contributes various extensions, such as debugging tools, deobfuscation plugins, and integration with other .NET tools.
Cryptography Tools:
It includes a cryptography tool window, aiding in cryptographic operations like encryption and hashing. This is particularly useful for analyzing security aspects of applications.
Features Of dnSpy
The versatile tool has multiple key features including:
| Decompiler | Disassembles .NET assemblies into human-readable C# code. |
| Debugger | Steps through .NET code line by line, sets breakpoints, and inspects variables. |
| Assembly Editor | Modifies .NET assemblies. |
| Expression Evaluator | Evaluate C# expressions at runtime. |
| Plugin System | Extends dnSpy with new features. |
Some other key features include:
- Supports multiple .NET frameworks
- Can be used to debug native code
- Has a built-in hex editor
- Can be used to generate reports
- Supports multiple languages
System Requirements
Before you begin using it, please make sure your computer is compatible or not for running the software smoothly. Here are the minimum and recommended system requirements:
Minimum System Requirements
- Operating System: Windows 7 or later
- Runtime: .NET Framework 4.7.2 or later
- Disk space: 30MB or more
- Memory: 1GB or more
Recommended System Requirements
- Operating System: Windows 10 or later
- Runtime: .NET Framework 4.8 or later
- Disk space: 1GB or more
- Memory: 4GB or more
Pros
Free and Open-Source:
If you are on a tight budget then dnSpy is the perfect one for you as it is a free and open-source tool. This added to its popularity. A survey conducted by JetBrains found that it is the most popular .NET decompiler, with over 70% of users surveyed reporting its use.
Powerful and Versatile:
The purposes of it range from debugging and reverse engineering to malware analysis. A user survey revealed that 95% of users are satisfied with the tool, and 90% recommend it to others.
Widely Used:
With over 1 million downloads, the tool boasts a substantial and active user community. This vast user base ensures that there is a wealth of support and feedback available, enhancing the user experience and reliability of the tool.
Actively Developed:
dnSpy is actively developed and maintained, regularly receiving new features and bug fixes. This commitment to improvement is reflected in the high user satisfaction and the tool’s enduring usefulness, as evidenced by data and user recommendations.
Portable
It can be run from a USB drive without the need to install it. This can help you achieve valuable computer memory to work more efficiently.
Cons
Can be slow for large assemblies:
dnSpy can be slow to decompile and debug large assemblies. This is because dnSpy needs to load the entire assembly into memory before it can start decompiling or debugging.
Some features are only available in the plugin system:
Some of the advanced features of it, such as support for debugging native code, are only available through plugins. This can make it difficult for new users to get started with dnSpy.
How to Use dnSpy for Debugging and Editing .NET Assemblies
Using dnSpy for debugging and editing is quite effortless. Here is a step-by-step guide for you to do it without breaking a sweat!
Download and Install:
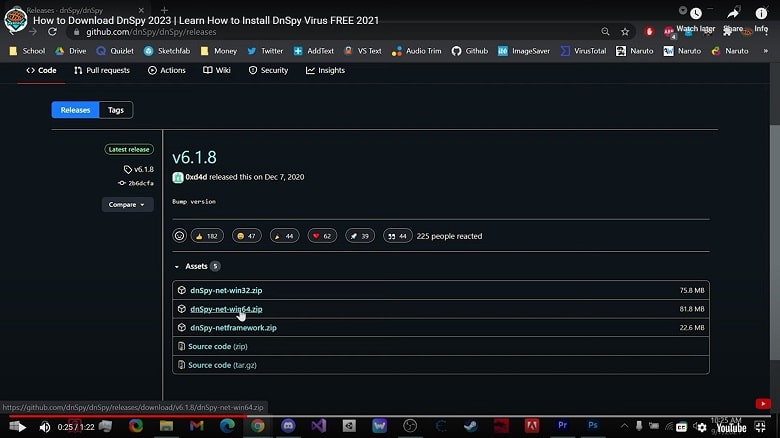
Loading Assemblies:
Now open dnSpy, load the target assembly (File -> Open), and explore its structure.
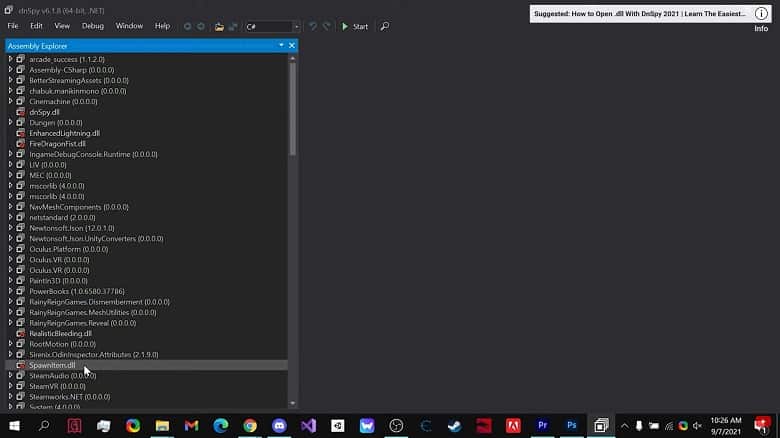
Debugging:
To debug, attach dnSpy to a running process or load an executable or DLL. Set breakpoints, inspect variables, and use the debugging features for effective troubleshooting.
Editing Assemblies:
dnSpy allows you to modify assemblies as caution is necessary when editing. Right-click on a method, choose “Edit Method,” and apply changes as needed.
Common Uses for dnSpy
According to Github, the common uses of the tool are listed below-
Debugging
- Debug .NET Framework and .NET Core assemblies, no source code required
- Set breakpoints and step into any assembly
- Locals, watch, autos windows
- Variables windows support saving variables (e.g. decrypted byte arrays) to disk or viewing them in the hex editor (memory window)
- Object IDs
- Multiple processes can be debugged at the same time
- Break on module load
- Tracepoints and conditional breakpoints
- Export/import breakpoints and tracepoints
- Call stack, threads, modules, processes windows
- Break on thrown exceptions (1st chance)
- Variables windows support evaluating C# / Visual Basic expressions
- Dynamic modules can be debugged (but not dynamic methods due to CLR limitations)
- The output window logs various debugging events, and it shows timestamps by default
- Assemblies that decrypt themselves at runtime can be debugged, dnSpy will use the in-memory image. You can also force dnSpy to always use in-memory images instead of disk files.
- Public API, you can write an extension or use the C# Interactive window to control the debugger
ASSEMBLY EDITOR
- All metadata can be edited
- Edit methods and classes in C# or Visual Basic with IntelliSense, no source code is required
- Add new methods, classes, or members in C# or Visual Basic
- IL editor for low-level IL method body editing
- Low-level metadata tables can be edited. This uses the hex editor internally.
HEX EDITOR
- Click on an address in the decompiled code to go to its IL code in the hex editor
- Reverse of the above, press F12 in an IL body in the hex editor to go to the decompiled code or other high-level representation of the bits. It’s great to find out which statement a patch modified.
- Highlights .NET metadata structures and PE structures
- Tooltips show more info about the selected .NET metadata / PE field
- Go to position, file, RVA
- Go to .NET metadata token, method body, #Blob / #Strings / #US heap offset or #GUID heap index
- Follow references (Ctrl+F12)
OTHER
- BAML decompiler
- Blue, light, and dark themes (and a dark high-contrast theme)
- Bookmarks
- C# Interactive window can be used to script dnSpy
- Search assemblies for classes, methods, strings, etc
- Analyze class and method usage, find callers, etc
- Multiple tabs and tab groups
- References are highlighted, use Tab / Shift+Tab to move to the next reference
- Go to the entry point and module initializer commands
- Go to metadata token or metadata row commands
- Code tooltips (C# and Visual Basic)
- Export to project
Tips for Using dnSpy Effectively
Now let us give you some handy insights to make your work easy and less complicated.
- To disassemble .NET assemblies into human-readable C# code try using the decompiler. You will understand the code easily and identify any problems.
- To step through the code line by line, set breakpoints, and inspect variables- use the debugger. This will help you to track down bugs and understand how the code works.
- Use the assembly editor to change .NET assemblies. Like fixing issues, adding new stuff, or getting rid of things you necessarily do not need.
- Use the built-in expression evaluator to check C# code while your program is running. This can be handy for testing out pieces of code or solving issues.
- Use the plugin system to extend dnSpy with new features. There are a number of plugins available that can add new features such as support for different programming languages or new debugging tools.
Comparison with Other Tools
Now why exactly you would choose dnSpy above other tools? To make it more coherent, let’s see the comparison table below-
| Feature | dnSpy | ILSpy | Reflector |
| License | Free and open-source | Free and open-source | Commercial |
| Operating system support | Windows, Linux, macOS | Windows, Linux, macOS | Windows |
| Features | Decompiler, debugger, assembly editor, plugin system | Decompiler, debugger, assembly editor | Decompiler, debugger, assembly editor |
| Pricing | Free | Free | Paid |
| Pros | Easy to use good documentation | Easy to useGood documentation | Powerful decompilerAdvanced debugging features |
| Cons | Some features are only available in the plugin system | Limited debugging features | CommercialNo Linux or macOS support |
So, dnSpy is a great pick because it is free and works on Windows, Linux, and macOS. It does a lot – like helping you understand code and fix problems. Others like Reflector cost money and do not work on all operating systems, while ILSpy is a bit limited when it comes to debugging. If you want a powerful, free, and flexible tool then this one is the way to go.
Real-World Applications of dnSpy
Let’s see some real-world situations where dnSpy has been a game-changer:
Microsoft:
Microsoft has used dnSpy to debug the .NET Framework and the Visual Studio IDE.
Pavel Bouvrie:
Pavel Bouvrie is the founder of dnSpy. He has used dnSpy to reverse engineer a variety of software programs, including the Steam client and the Minecraft game launcher.
WannaCry Ransomware
Security researchers used dnSpy to analyze the WannaCry ransomware. This ransomware caused widespread damage in 2017. By analyzing the WannaCry ransomware, security researchers were able to develop a way to decrypt files that had been encrypted by the ransomware.
Conclusion
Software development can be a little demanding sometimes but with dnSpy as your companion you can take your skills to the next level. It is the trusty tool you can rely on to decompile .NET assemblies and unravel coding enigmas. So, keep dnSpy in your toolbox, and let your programming adventures continue on a high note. Happy coding!
| App Name: | dnSpy |
|---|---|
| Version: | 6.1.4 |
| License: | Free |
| Publisher: | 0xd4d |
| Category: | Developer Tools |
| Operating Systems: | Windows 2000 / Vista / Windows XP / Windows 7 / Windows 8 / Windows 10 / Windows 11 |
| Language: | English |
| File Name 32 Bit: | dnSpy-net-win32.zip |
| File Size 32 Bit: | 75.8 MB |
| File Name 64 Bit: | dnSpy-net-win64.zip |
| File Size 64 Bit: | 81.8 MB |
| VirusTotal Hash Code: | 78d855aef02d87195ddde4f4a89f16f03708e66ec8282cf8eb9ecc89dd469f6c |
| VirusTotal Scan Report: | Check Report |
| Date Published: | 18, November 2021 |
| Date Modified: | 04, December 2023 |
Here are some latest released apps
Explore latest Blog Posts
Every business needs to keep pace in today’s fast-changing digital landscape. It is the businesses […]
Abstraction of computing, storage spaces, and networking resources, are the key features of virtualization technology. […]
Smartphones have gotten bigger and bigger and so did their batteries. While you won’t get […]
React has emerged as a leading technology for building interactive and user-centric applications. You have […]
Nowadays, finding someone’s email address has become much more straightforward, thanks to various online tools. […]
Crafting a Strategic Email Workflow The most important aspect that affects deliverability is your email […]
Do you want to know whether your customer experience strategies are effective? Look at your […]
In the past, investors relied on phone calls to navigate the complicated workings of stock exchanges. […]